Firewall Components: Application Level Gateways
Proxy - the agency, function, or power of a person authorized to act as the deputy or substitute for another;The idea that stands behind Proxy component of a firewall design is not to allow direct TCP (UDP) connection between client software on the Local Network and server software on the Internet or vice versa (the client software on the Internet and server software on the Local Network).
Instead the direct connection is broken into two separate connections. The proxy program acting as an intermediate.
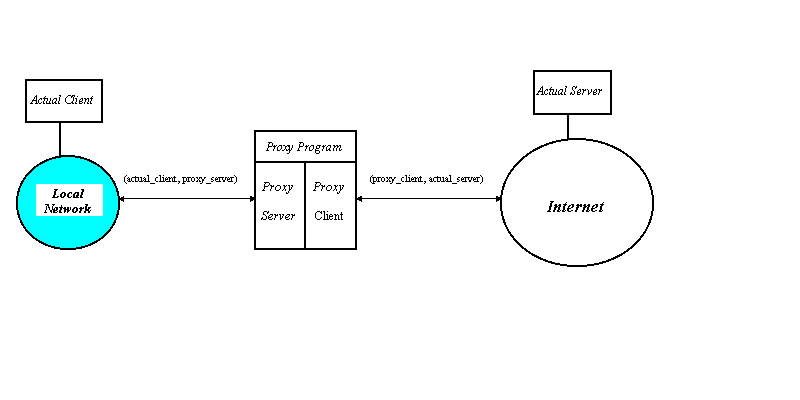
Figure 6 : Operation of Application Level Gateway.
As it relays the traffic between actual client and actual server it does checks and access controls that typical client and server software do not support.
Proxy program must implement enough of the client and server part of application protocol to accomplish the following:
- Accept client sessions and appear to them as a server;
- Receive from the client software the name of the actual server;
- Contact the actual server and appear to it as a client;
- Relay all the data from the client to a server;
- Perform access control function, that is according to Security Policy chosen for a site it must reject potentially dangerous connections;
First of all the external hosts should not know about the Local Network topology and thus should not know the IP address or name of the host machine on the Local Network on which a specific server may be located. External hosts should only know about the Application Gateway machines.But if external hosts does have this information it could try to contact the internal server. To prevent this the IP connectivity between Local Network and the Internet must be broken. This can be achieved in several ways please refer Firewall Architectures part of this document.
Once more the IP connectivity between Local Network and the Internet must be broken.In addition to this the client software on the Local Network must know how to contact the proxy server instead of the actual server on the Internet. To accomplish this two proxy technologies exist: classical proxy technology and transparent proxy technology. For more information on classical and transparent proxies please refer to RFC 1919.
In classical proxy technology either the client software is modified or the user is instructed to follow special setup procedures in order to make call to the actual server through the proxy server.
In transparent proxy technology the routing tables of the Local Network are configured in such a way that all the packets destined for the external servers come to the Application Gateway machine and proxy program knows how to intercept these packets and to form two connections (actual_client, proxy_server) and (proxy_client, actual_server).
For more information on topics covered in this section please refer to following resources:
- Chapman, Elizabeth D. Zwicky,
"Building Internet Firewalls",
O'Reilly&Associates, 1995
Availability: offline
- William R.Cheswick, Steven M.Bellovin,
"Firewalls and Internet Security: Repelling the Wily Hacker",
Addison-Wesley Publishing Company, 1994;
Availability: offline;
- M.Chatel, RFC1919,
"Classical versus Transparent IP Proxies",
Summary: this RFC describes how classical and transparent proxies operate and differences between them, can be used as reference material for proxies;
Availability: online;
![]()