Contents
The concept that stands behind the firewall approach is to allow local users to enjoy full network services within their local network and some useful services provided by the Internet while controlling outsiders' access to the local network resources.Firewall approach achieves security by isolating a specific segment of Internet topology( further Local Network) from the rest of the Internet and controlling all the traffic that comes to and leaves the Local Network.
To control the network traffic each connection of Local Network to the Internet is equipped with a firewall. Firewall's goal is to inspect and control all the traffic between the Local Network and the Internet. The traffic must be handled in such a way that all potentially "dangerous" traffic be detected and dropped and if necessary logged. What traffic is "dangerous" for the Local Network is determined by the Security Policy adopted for the site.
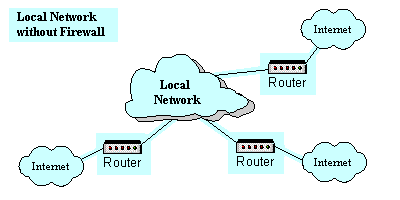
Figure 1: Local Network with and without firewall.
The result of firewalling the Local Network can be viewed as follows. In the case of Local Network directly connected to the Internet without any firewall, the entire network is subject to the attack. Consider a large organization with thousands of hosts. If every host is allowed to communicate directly with the outside world, the attackers will find the weakest of the hosts and penetrate it. If one of the hosts is penetrated it is not difficult to penetrate all the other hosts on the network using the resources of that compromised host. Practical experience shows that it is very difficult to ensure that every host on the network is secure. One badly chosen password and all the network security can be compromised. On the other hand if Local Network is guarded by the firewall there is direct access only to selected subset of hosts and the zone of risk is often reduced to the firewall itself or a selected subset of hosts on the network. In some sense firewall are not so much a security solution as they are a response to the engineering/administration problem: configuring a large number of hosts systems for good security.
In this short overview we did not described exactly what kinds of attacks can threaten the Local Network.You can refer to following resources to find this out:
- S.M.Bellovin,
"Security Problems in the TCP/IP Protocol Suite";
Summary: this article describes various security holes in TCP/IP protocol stack and how these problems can be exploited to attack a network;
Availability: online;
- S.M.Bellovin,
"There Be Dragons";
Summary: this article describes the attack attempts at the AT&T firewall system;
Availability: online;
- The CERT coordination center maintains archive of the reports of known security attacks and solutions to prevent them;
Availability: online;